Main Features
The main characteristics of this program are that it will allow us to perform a forensic analysis of the network with the capture of PCAP traffic, although we will also have the ability to sniff all the traffic from the wired network card or WiFi, however, it is compatible with WireShark because it is the most widely used protocol analyzer In the world. Other important features are that it allows you to extract passwords from data capture directly in plain text, without having to examine all the traffic in detail, it is completely automatic. We can also create a network map, rebuild TCP sessions, we can extract hashes of encrypted passwords and even convert them to Hashcat format to try to crack them later with this software, and perform a brute force or offline dictionary attack.
The primary goal of this BruteShark software is to provide a comprehensive solution for IT security researchers, network and system administrators to identify potential problems, vulnerabilities, threats on the local network, and other security flaws that a future attack could lead to. This program is available in two obviously different versions, we will have a GUI version for Windows, and we will also have a command line version (we will work in Terminal) compatible with Windows and Linux systems. Of course, this software can be used to analyze network traffic for Windows, Linux or macOS computers without any problem.
This program is able to extract and decrypt usernames and passwords from protocols such as HTTP, FTP, Telnet, IMAP, SMTP and many other protocols, i.e. all protocols that do not have end-to-end encryption such as HTTPS, FTPES, SSH and many others. This program is also able to extract hashes and convert them to Kerberos, NTLM, CRAM-MD5, HTTP-Digest formats and more, of course, you will be able to create a visual network diagram with different users and network devices, and it is also able to extract all DNS queries made (as long as No encrypted DoH or DoT was used), and it allows rebuilding TCP and UDP sessions, sculpting files and even extracting VoIP calls if SIP and RTP protocols are used.
Once we know all the features of this program, we will see in detail how it works.
Download and install on Windows
If you are interested in installing this program on Windows, you can download two versions:
The only prerequisite is to install WinPcap or NPcap, it must be remembered that if you have WireShark installed, you will install one of both drivers. You must also have the .NET Core Runtime installed in order to run it.


If you intend to install this program on Linux systems, you will need to install libpcap, then we will execute the following commands:
find /usr/lib/x86_64-linux-gnu -type f | grep libpcap | head -1 | xargs -i sudo ln -s {} /usr/lib/x86_64-linux-gnu/libpcap.so
wget https://github.com/odedshimon/BruteShark/releases/latest/download/BruteSharkCli
./BruteSharkCli
Once installed, we start executing it, we must remember that we will only have a graphical user interface in Windows operating systems, in Linux we will have to execute commands by the console.
How does BruteShark work
This program works in a really simple way, the first thing to do is upload the PCAP file to analyze it, then analyze the file or files we have uploaded. We also have the ability to build TCP and UDP sessions, and even start capturing network data. If you do not have any capture to analyze, you can use this program instead of using WireShark, export the capture in PCAP and import it later in this program. This way, we can do it more easily with a single program.
In the right part of the program is where we can see the user credentials that are in the network traffic, they will show us both passwords in plain text (if protocols without encryption are used), and it will also show us the hash if we use Kerberos, NTLM and other protocols we have discussed Previously. In this section we will also be able to see network topology, sessions executed, DNS requests and finally we will find potential files captured and VoIP calls if we do any of them.
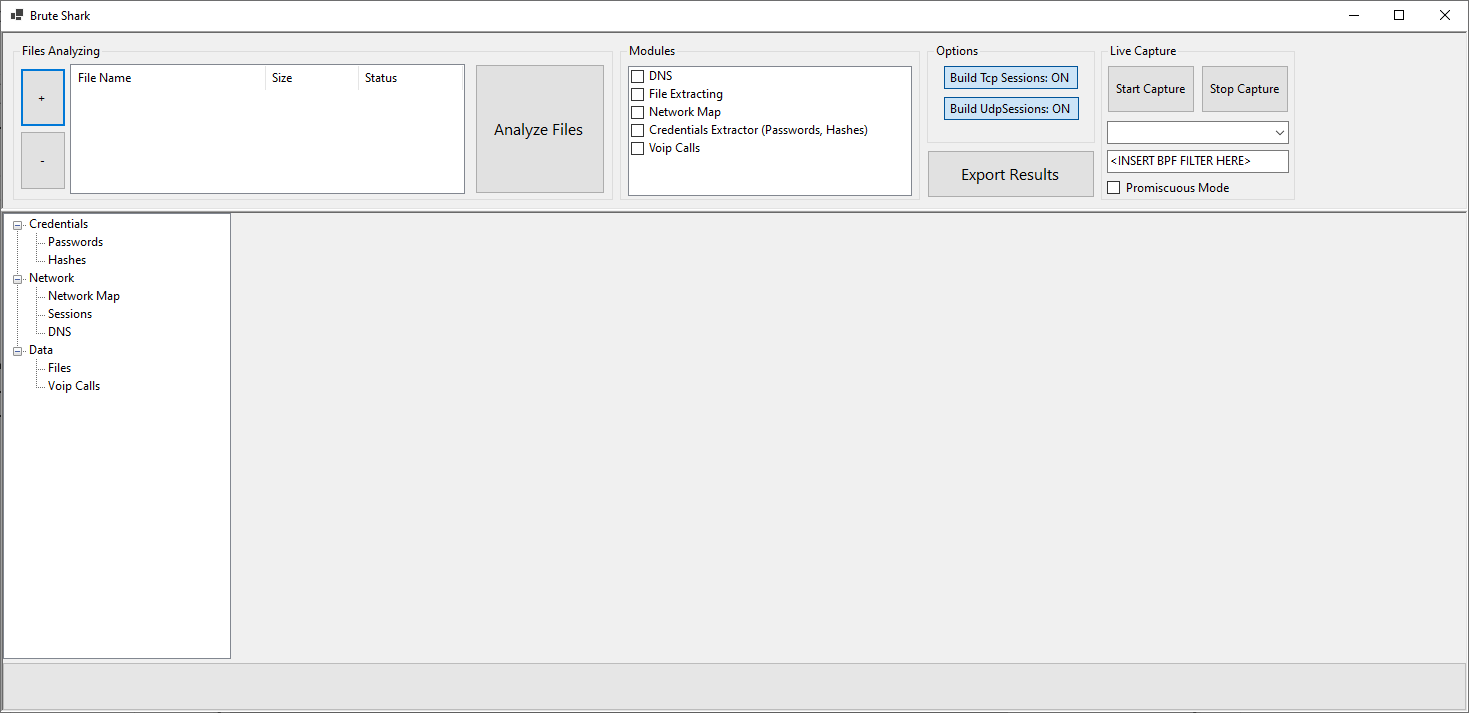
If we want to capture network traffic from any of the network interfaces, it is absolutely necessary to run BruteShark with administrator permissions, otherwise we will not even get wired and WiFi network cards on our computer.

We must also keep in mind that if we are going to use WireShark, we have to export the snapshots in PCAP format and not PCAPNG as it happens by default, because we will get the following error. We will have two options, either use WireShark and save as PCAP, or use the tshark program through the command line.
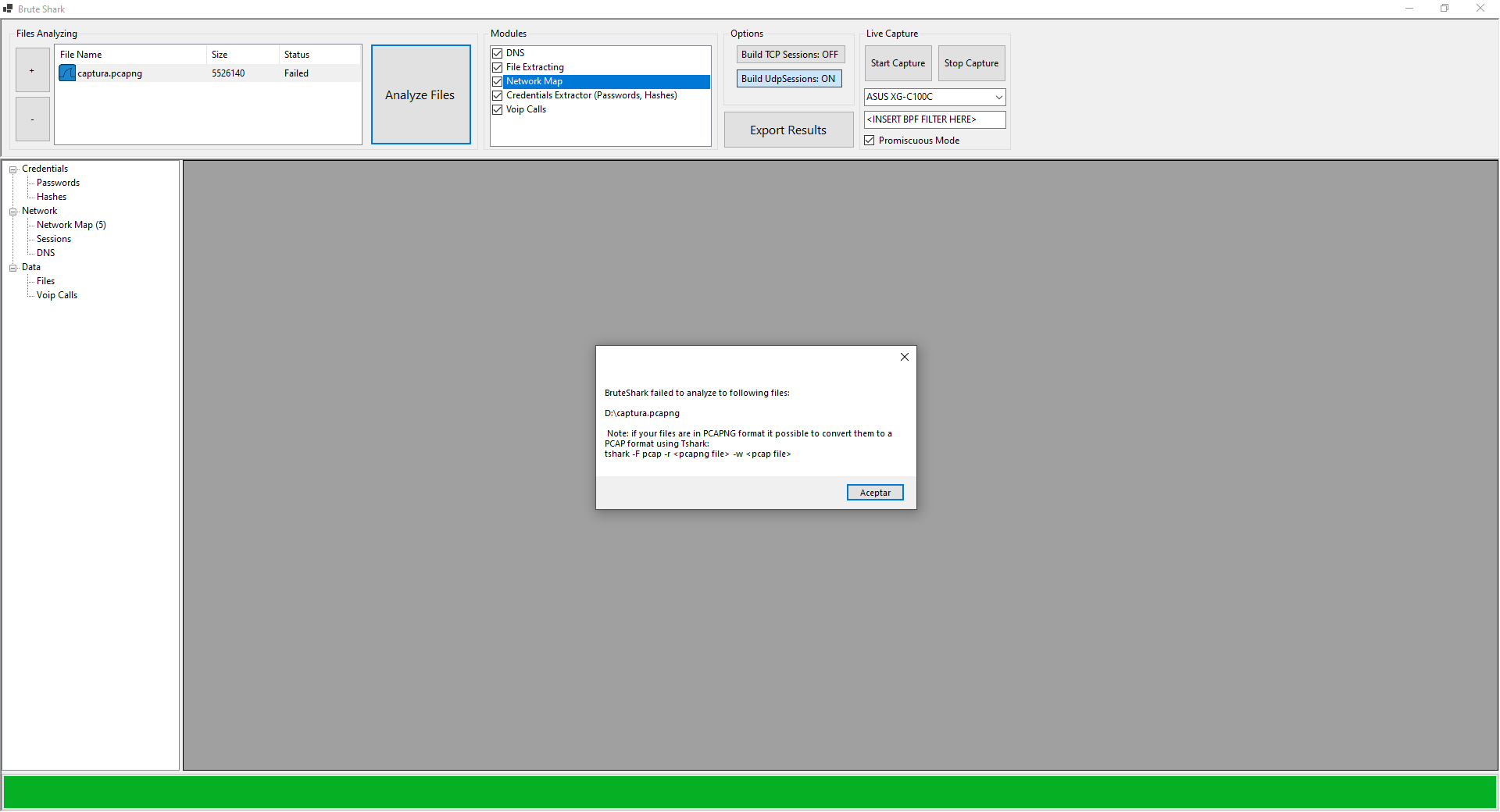
When we open a PCAP compliant capture, we have to click on “Analyze Files” and it will start analyzing the capture, this can take anywhere from a few seconds to a few hours, depending on the size of the capture that BruteShark has to analyze.
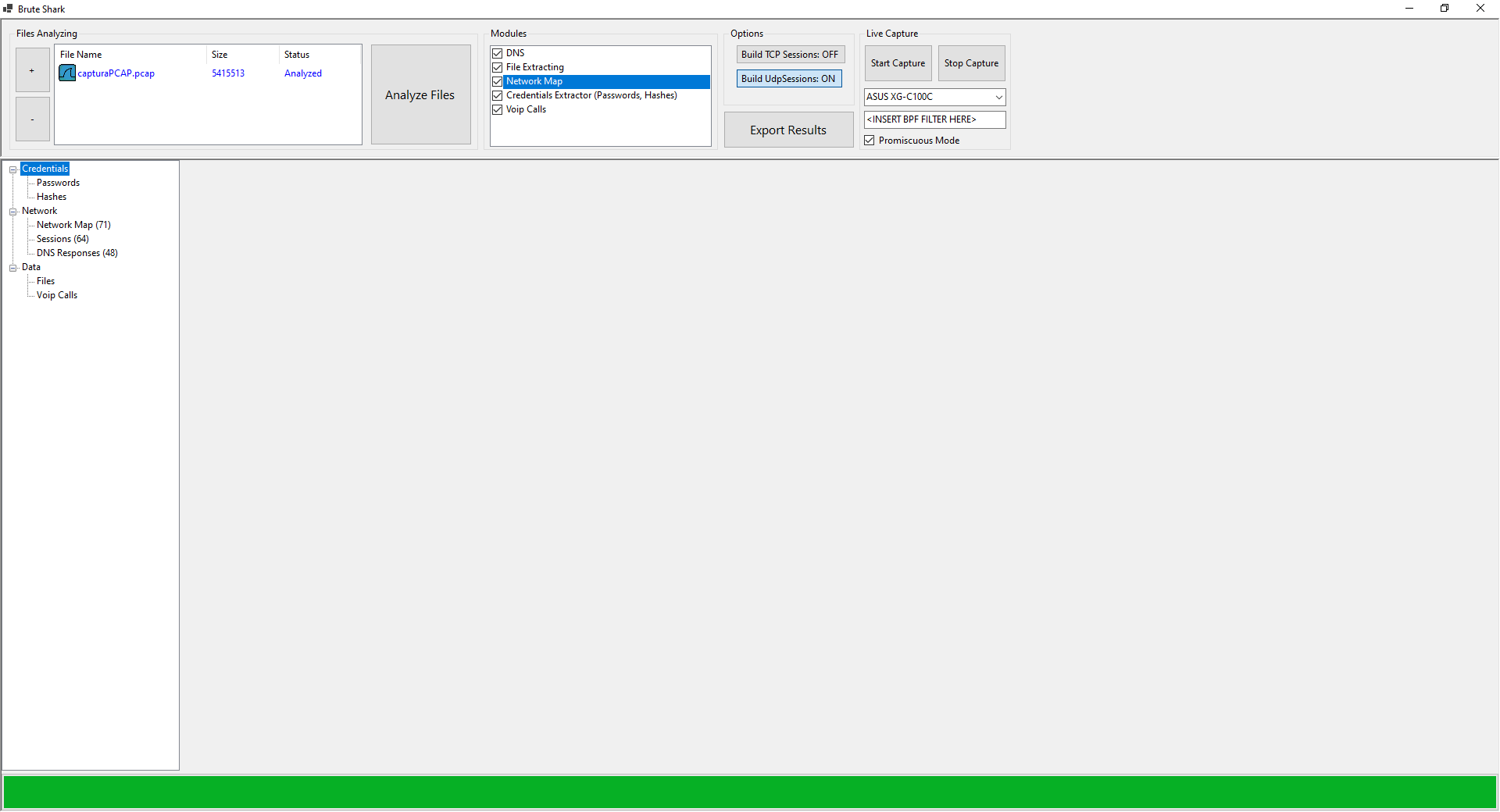
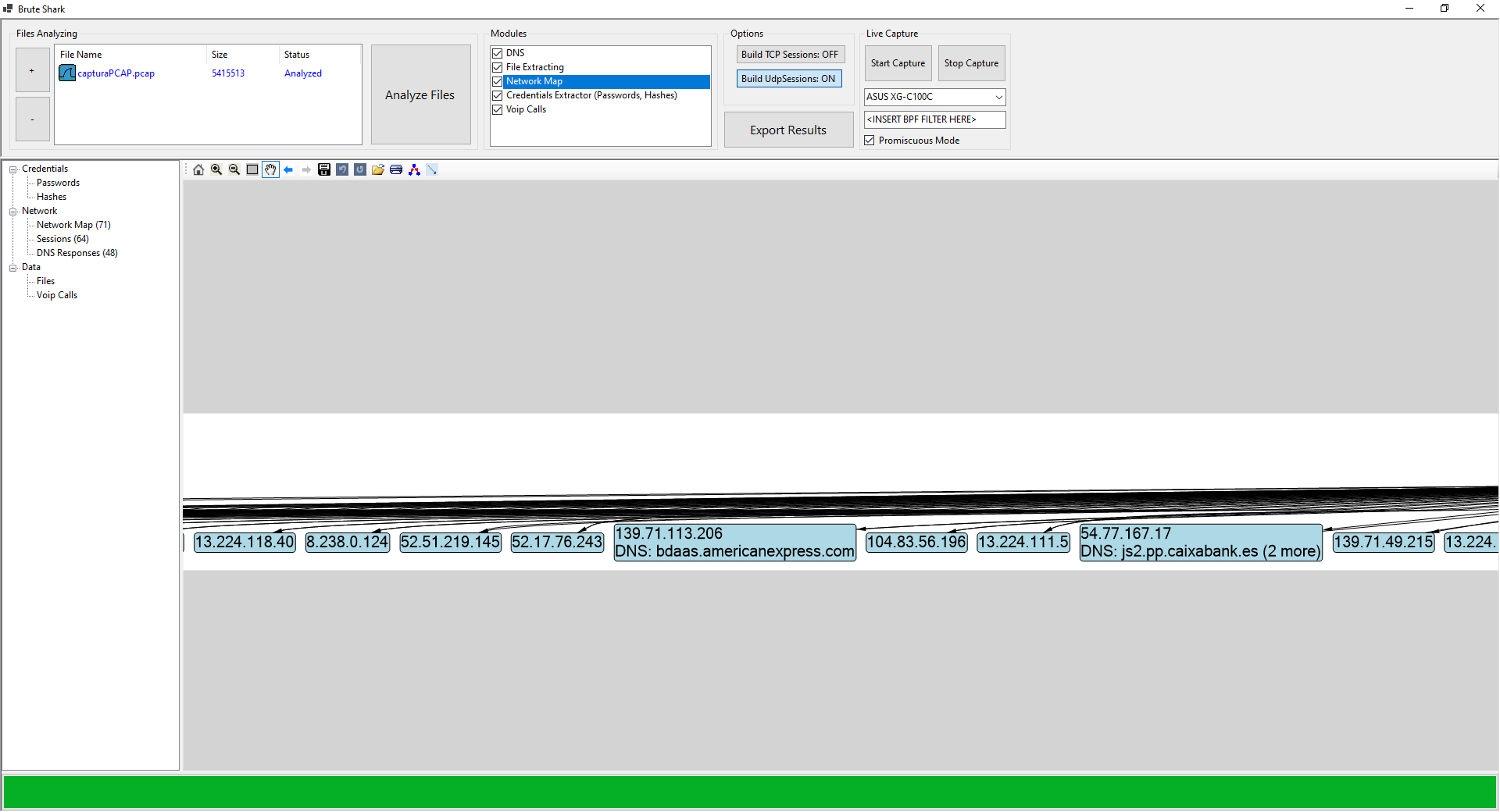
In our case, we always used DNS and HTTPS connections, thus, no password or password hash was captured by not using Kerberos or NTLM. What we can see is the network map of all the requests made.
We can also see all the sessions made from our computer, with the corresponding source and destination IP address, as well as the source port and destination port.

Finally, we can see all the DNS requests made while capturing the data, for example, our website, American Express, Interactive Brokers and many more that you can see below:

As you have seen, using this program to extract credentials, DNS requests, view network map, sessions, and even view files or information on VoIP calls is really easy to use, we will get this same information by offering WireShark data capture, but it will take longer if we don’t use filters occasion, so BruteShark makes this easier for us.

Lifelong foodaholic. Professional twitter expert. Organizer. Award-winning internet geek. Coffee advocate.

